
HaxHQ is probably the best Nessus reporting tool
HaxHQ was created in 2019 partly because we constantly had to import huge Nessus scans which caused Dradis to grind to a halt. HaxHQ processes a 60MB .nessus file in under 7 seconds (Dradis Pro does the same file in 8 min) and it is a game changer if you need to process many or big scans. It provides 2 options for merging overlapping findings and a full featured library which allows customising default Nessus texts on the fly.
Challenges in generating customised reports from Nessus scans
Nessus is an excellent tool which is easy to use, has low false positive rate and very good detection rate when it comes to general scanning. The reports it produces do require some expertise to interpret and can or even should be improved before presenting vulnerability scan results to cusomers. When presented with a large report, people often struggle to organise and prioritise remediation.
Whether you need to modify texts on the fly, replace or add CVSSv3 score and vector information or deduplicate external findings which are also present internally it is all automated.
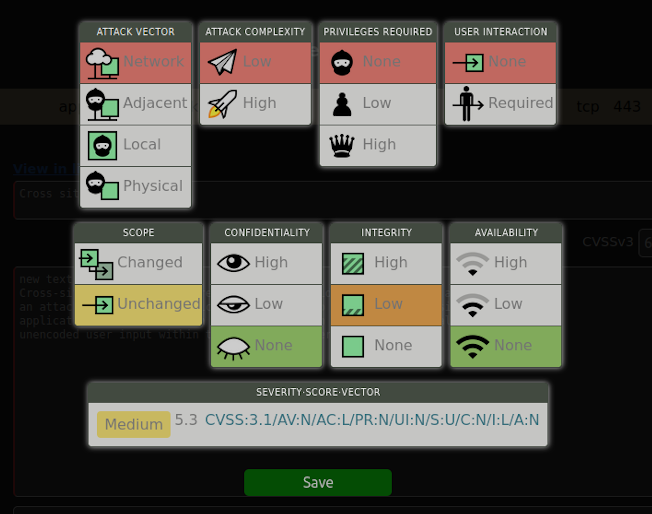
Calculating CVSS values
Nessus doesn't consistenlty provide CVSS information for vulnerabilitie. It can list CVSSv3, CVSSv2, both or no CVSS information at all. HaxHQ allows you to easily calculate the score and vector and store the values alongside the findng in your content library for reuse.
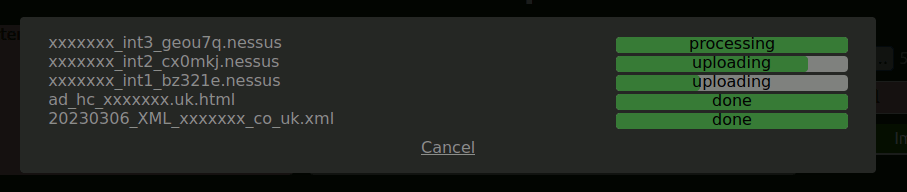
Large .nessus files
When scanning large networks, the size of nessus scan files exceeded 500MB on occasion and was regularly over 100MB. This can cause issues when uploading because of maximum request size settings and timeouts. When processing and displaying results it can choke a reporting tool which is not optimised for handling large data sets. HaxHQ not only deals with such files easily, it allows you to upload multiple files in parallel, inculding from different scanners.
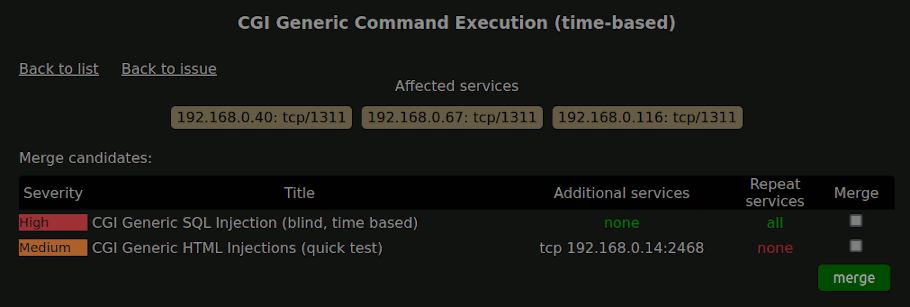
Overlapping findings bloating the report
Even if you untick the 'Show missing patches that have been superseded' setting, which you should, overlapping findings are common. For example, the same vulnerability can be listed as an HTML injection and XSS, or the same service can be affected by very similar vulnerabilities listed separately in nessus. Finally, when a missing patch causes both a critical and several lower severity vulnerabilities, listing just the critical issue can make sense as much as the resolution is the same for all.
HaxHQ allows easy merging of such vulnerabilities to remove bloat and make the report easier to read and action.
Very large 'affected hosts' lists
In a large network, there can be hundreds of hosts affected with the same vulnerability, for example support of TLS 1.0. If you are listing the affected hosts in the detailed issue description, this can result in many pages in the report containing just tables with affected hosts. Readability aside, this can cause Word or Libre Office to become very unresponsive. The way HaxHQ solves this is by automatically exporting such lists to an appendix, and then referencing that appendix in the issue listing.
Let us help you work more efficiently
Whatever challenges you are facing with the specific scanning tools you need to import from and regardless of the desired report format, we will work with you to provide fast and easy to use report automation. Please contact us to book a demo. While we would prefer to be there to answer questions and guide you, you can have a look at the demo instance directly as well.

Try HaxHQ for yourself
This project is now on the back burner and the automatic trial is disabled. Please contact me if you would like access.
